Microsoft is ramping up defenses against malware coming from the internet to a computer. They are working on an XL add-in for Microsoft 365 customers which will automatically block any files of harmful nature coming from the Internet.
In recent years there has been a rise in malware attacks using this infection pattern. Microsoft has decided to end it for good by not taking preempting action against such threats.
They will block all the incoming XLL add-ins coming from the internet because there has been a rise in malware attacks in recent months, Microsoft said in the roadmap item.
What is really happening?
Attackers are using XLL to push various malicious files for phishing attempts which appear in the form of documents or download links from trusted contacts in the garb of partnerships, guides, etc.
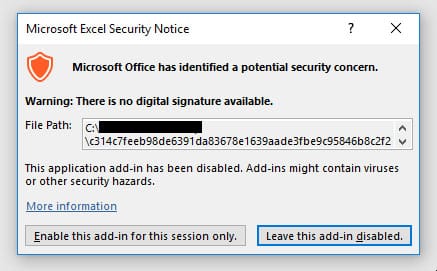
Once you click on a XLL as it is an executable file, Microsoft sends a security notice warning you from opening the file. The warning message reads “a potential security content”, “… add-ins might contain viruses or other security hazards”.
If you let it run the malicious add-in then it will deploy malware on your device. Therefore you should avoid only open XLL add-ins coming from trusted sources.
What is Excel XLL Add-in?
An Excel add-in is a program that adds extra features to the Microsoft Excel program you already have. These features can be anything from extra formulas for calculations, to new ways to visualize data, to tools that make it easier to manage and organize your spreadsheets.
For example, an add-in might include a set of financial formulas that you can use to calculate things like interest rates or loan payments. Another add-in might add new charts or graphs to Excel, making it easier to create professional-looking visualizations of your data.
When to expect the update?
Microsoft says that we can expect the update by March for desktop for users in current, monthly enterprise, and semi-annual enterprise channels.
Image credit – HP Wolf Security Blog